How to assess risk with a control matrix
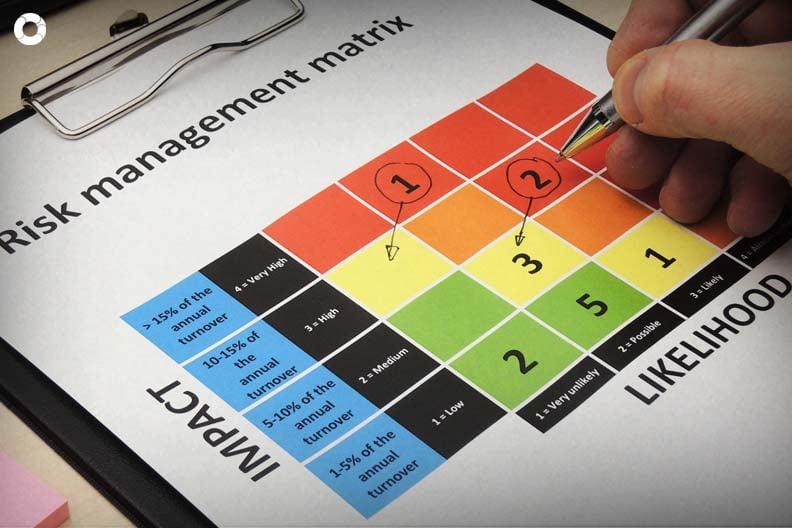
We have already explained how to identify and rate risks according to the established scales. Now we will show you how to assess them using a control matrix.
1. We have said that in order to design a control matrix components are arranged in rows and threats in columns. The former indicate the resources to be protected and the latter are the negative events that affect them. In risk management, it is important to bear in mind that both components and threats must first be prioritized in the rating process.
If there is a repeated score, the same value is assigned to two different cells in order to establish priorities that will then mark the zones according to the risk they generate, as high, medium or low. Following the example explained here, the matrix should look like this:
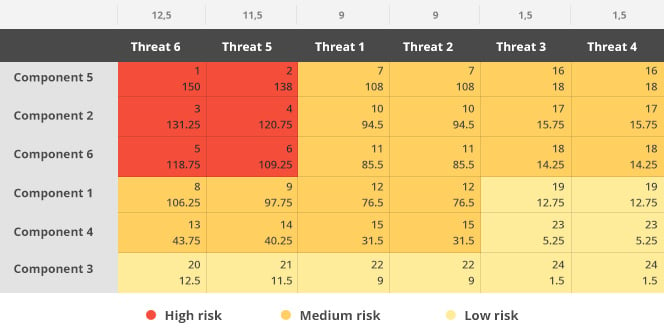
2. A matrix of threats, components and controls is then prepared, which is one of the most common methods for assessing risk. The latter are listed and added on the intersection that controls the threat affecting a component.
At this point, it is imperative to determine which is the most sensitive cell, which in the case of the control matrix will always be located in the upper left corner. It must also be defined whether the controls applied are sufficient for each cell, particularly those at high risk. If they are not sufficient, new controls should be proposed. This way, the least sensitive cell is established and a review is conducted to know whether or not the controls applied are excessive.
3. After this, an analysis will be conducted according to the greater or lesser number of controls and it will be established whether they are sufficient or excessive, taking into account the need to control the threat and protect the component at all times.
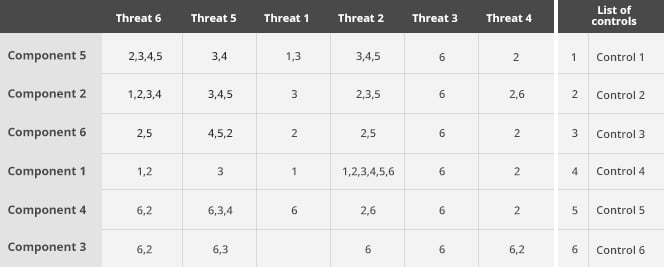
4. The components are as follows, considering the sufficiency and effectiveness of the controls applied.
5. Finally, the threats are examined to determine whether or not they are properly controlled. The matrix of threats, components and controls should look like this:
You May Also Like
These Related Stories

Prevent money laundering by knowing your customer

Pirani earns 14 new badges on G2

How to manage credit risk

Interbolsa case study: 6 years later

What is a good key risk indicator (KRI) like?


No Comments Yet
Let us know what you think