Pirani Academy
Learn more about risk management
Highlights of the week

Podcast | Risk Culture Is Built by People, Not Policies
Listen now

FREE E-BOOK
Download now
Free template: Prompt generator for risk management
Download now
Every third Wednesday of the month, you'll learn everything you need to know about Risk Management. Next Class: Emerging Risks 2026: What Risk Leaders Must Prepare for Now
![]() January 28th |
January 28th | ![]() 11:00 a.m. GMT-4 |
11:00 a.m. GMT-4 | ![]() Live
Live

Register for FREE at the Risk Management School!
Check out our classes!  | 4 free classes
| 4 free classes

Africa’s New Regulatory Horizon
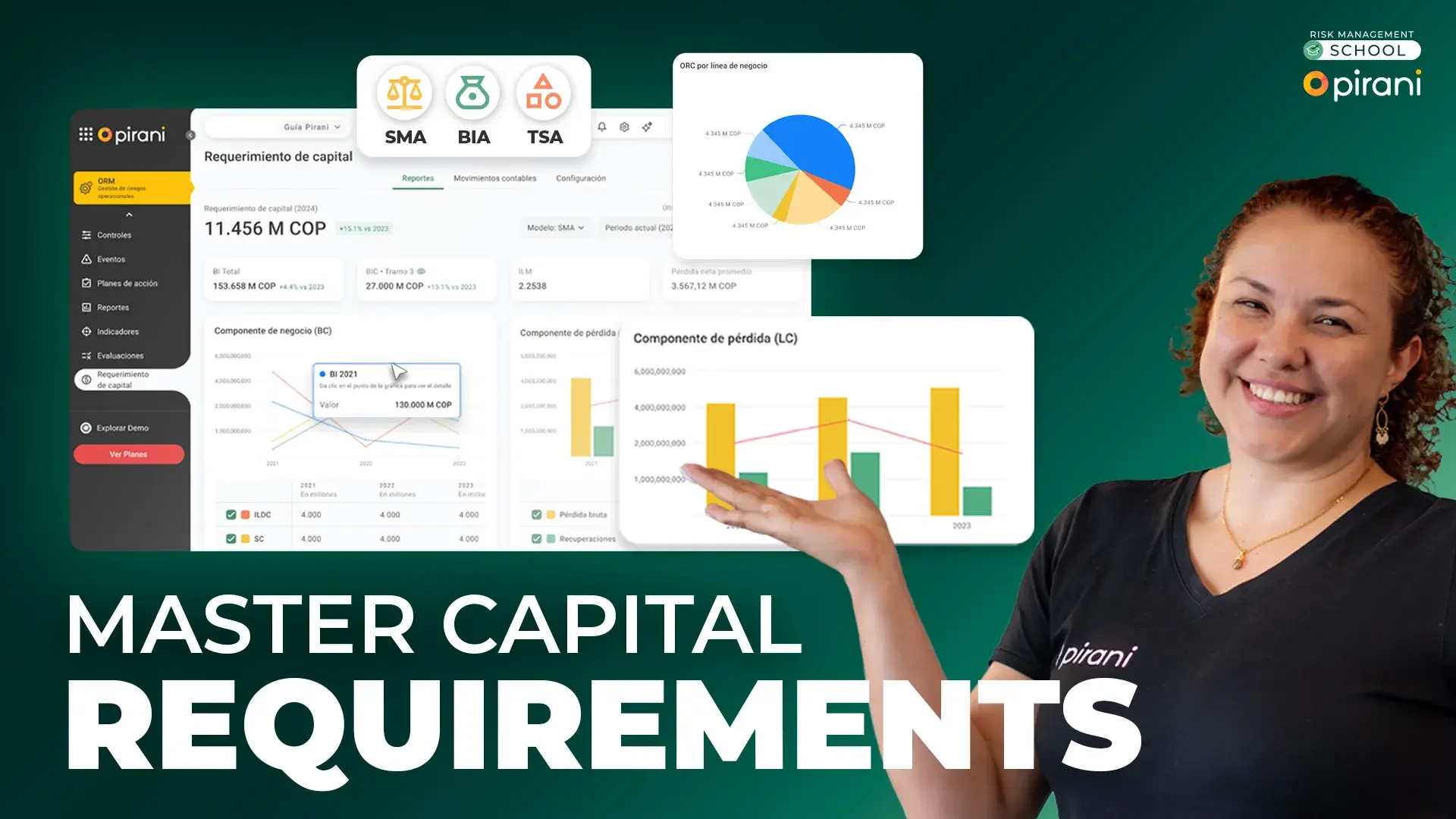
How your organization can calculate Capital Requirements

The Bowtie Method: Visualizing the Path from Causes to Consequences
Blog Pirani
Stay informed and make good decisions in your organization. Enter our blog and learn more about risk management, LAFT risk prevention, information security, regulatory compliance and other topics of interest.

How Director Accountability Will Shape African Regulation in 2026
For much of the past decade, regulatory conversations in Africa focused on frameworks, policies, and institutional capac…

Why Third-Party Risk Will Be the First Domino to Fall in 2026
In 2026, many organizations in North America will discover that their most serious operational failures did not start in…
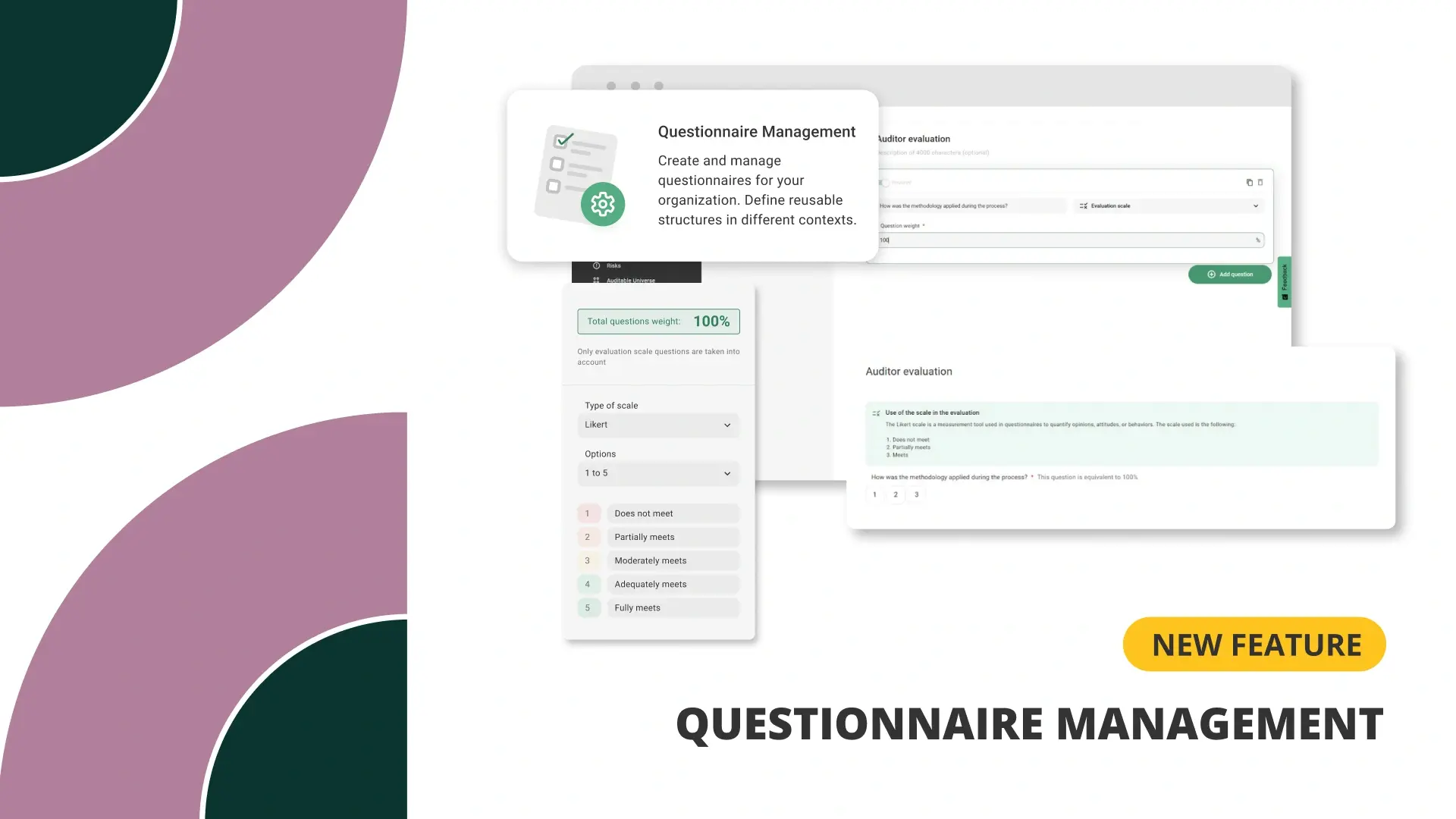
Questionnaire Management in Auditing
In auditing, what is not properly evaluated and documented can hardly be improved. Having formal mechanisms to measure p…
Next webinar

The Hidden Costs of Poor Risk Management
June 13th | 10:00 AM (UTC-4) US Florida
Poor risk management doesn’t always show up in headlines, but its consequences quietly erode value every day. From overlooked compliance gaps and fragmented processes to misaligned incentives and delayed decisions, the signs are often subtle until a crisis hits.
Register for freeView events

The Hidden Costs of Poor Risk Management:
Uncover what poor risk management really looks like, highlight the red flags leaders should watch for, and reveal the true price of inaction.

First steps in risk management:
6 ways to identify them, how to analyze risk, and the six strategies to deal with risk.

Cybersecurity and ISO 27001:
Protecting Information and Intellectual Property in a Digital World.
eBooks
Download our free PDF eBooks. In our library you will find valuable content that we update continuously and will help you to deepen your knowledge on topics related to risk management.
Videos
Do you want to know more about risks? In Pirani's videos you can learn important aspects of the risk world in minutes and learn more about our software.
Pirani Explains
Download content of interest to you on each of the components of risk management so that you can understand a little more about the processes that must be carried out in a company to avoid or mitigate risks.
See all explains →

The New African Regulatory Horizon
Africa is undergoing a major regulatory shift that is redefining risk governance, financial integrity and operational resilience. Rising standards in supervision, AML/CFT, cyber and climate oversight are shaping a more integrated and forward-looking regulatory landscape—one that demands stronger governance and modernised risk management.

Risk Management Guide from Scratch
Navigating the world of risk management can seem daunting at first, but we're here to simplify the path for you. This step-by-step guide is designed to help you easily understand the essentials of risk management. Whether it's identifying risks or implementing strategies to manage them, this comprehensive and straightforward guide will provide you with the knowledge you need to effectively protect your business.

Understanding SOC 2: What It Is and Who Oversees It
Discover what SOC 2 is, an essential tool at a time when cyberattacks such as ransomware, phishing, and vishing are proliferating.
These issues are a challenge for companies regardless of their size or the sector in which they work. We will learn what SOC 2 is, who regulates it, and why it is so important to keep companies secure. In addition, we will look at the principles of trusted services, how SOC 2 is implemented and evaluated, its parameters, and its validity.
Create the content you always wanted to read or watch
Would you like to write an article, record a podcast or give a webinar? Tell us a little more about yourself by filling out the form and we will contact you to give you all the details on how you can share your knowledge with our community.


