Manage the threats and vulnerabilities of your information assets.
 Effective information security management requires identifying and addressing threats and vulnerabilities to protect information assets and maintain information integrity, confidentiality, and availability.
Effective information security management requires identifying and addressing threats and vulnerabilities to protect information assets and maintain information integrity, confidentiality, and availability.
Therefore, now in Pirani, threats and vulnerabilities will have a specialized section where you can create and manage your threat and vulnerability records, associate them with assets and risks, and assign a responsible person to monitor them in one place, taking into account the good practices of ISO 27001.
Threats: These are external events or situations that can cause direct or indirect damage to information security. They can be natural disasters, hacker attacks, or technical failures.
Vulnerabilities: These are internal weaknesses or flaws in security systems or processes that could be exploited by threats or allow an attacker to affect information security. They can be weaknesses in policies, software, and more.
These are the benefits and features you will find
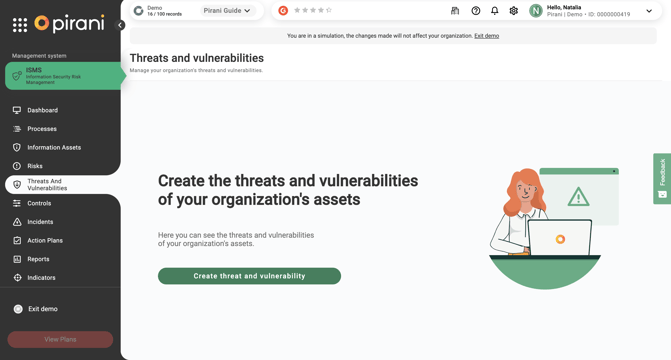
Identify threats and vulnerabilities.s
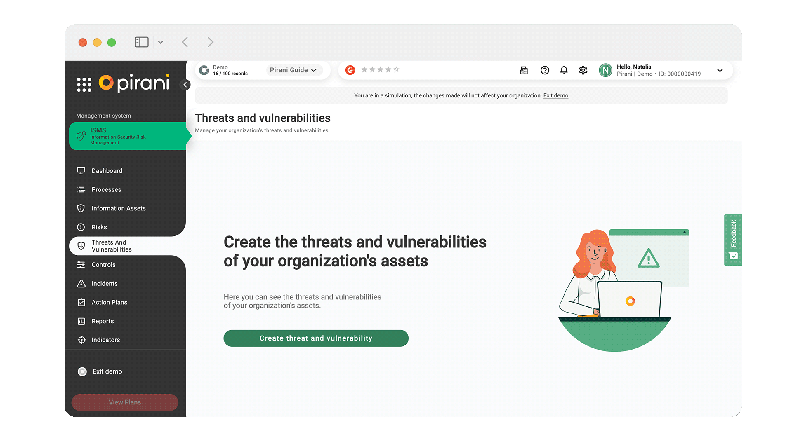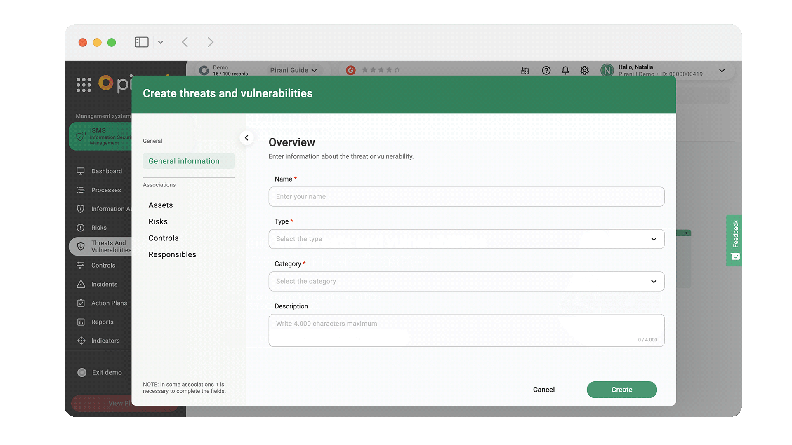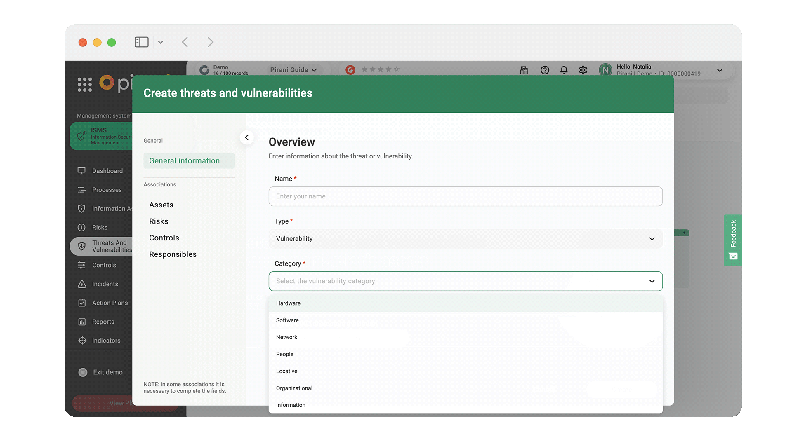
Now, you can create, edit, and adequately monitor threats and vulnerabilities of information assets with the new specialized section "Threats and Vulnerabilities." You will be able to assign a name to identify each record, indicate whether it is a threat or a vulnerability, choose from the different types of categories for each record, and add a description to guide the user on the nature of the record.
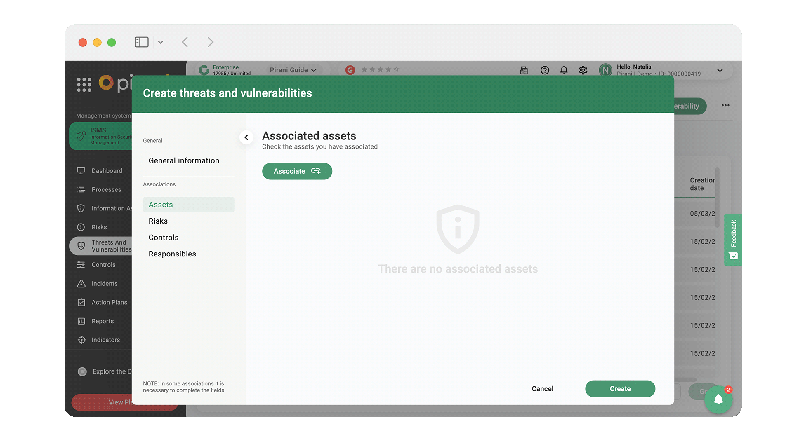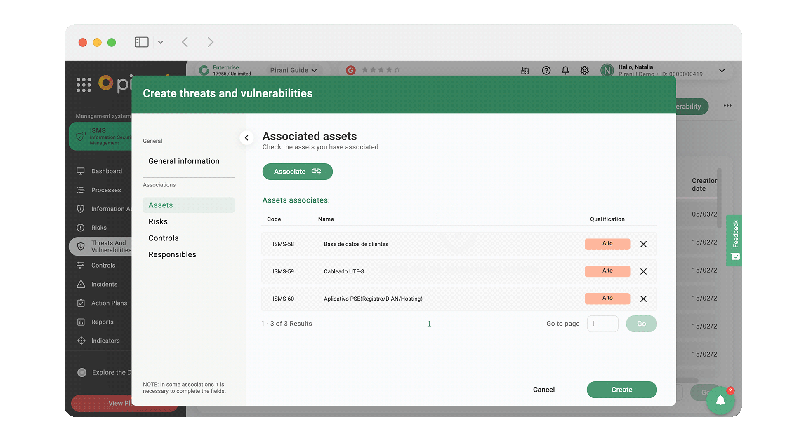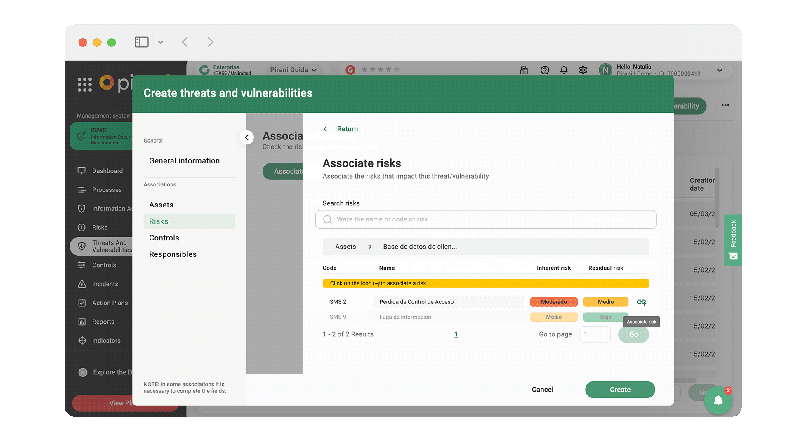
Make associations
Now, you will be able to associate these records with the corresponding assets, risks, and controls from the threats and vulnerabilities section to monitor internal weaknesses and external events that may affect the organization's information assets and objectives. You will also be able to associate a responsible person with each threat and vulnerability created so that he/she can supervise its evolution.
Wait, don't you still use Pirani? 👀
Discover how simple it is to manage your assets' threats and vulnerabilities with Pirani. Try our tool for free, and tell me in the article's comments what you think about our information security management system section.
Bulk Import
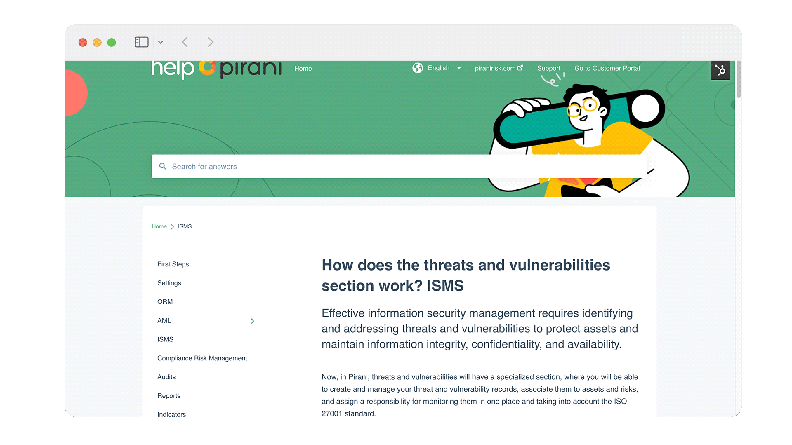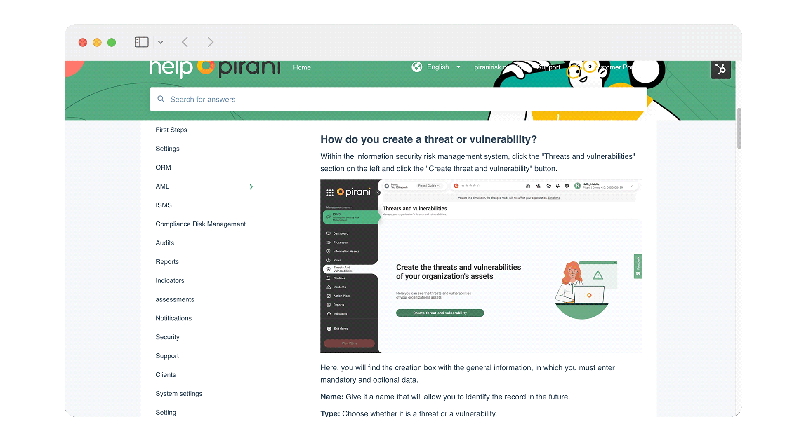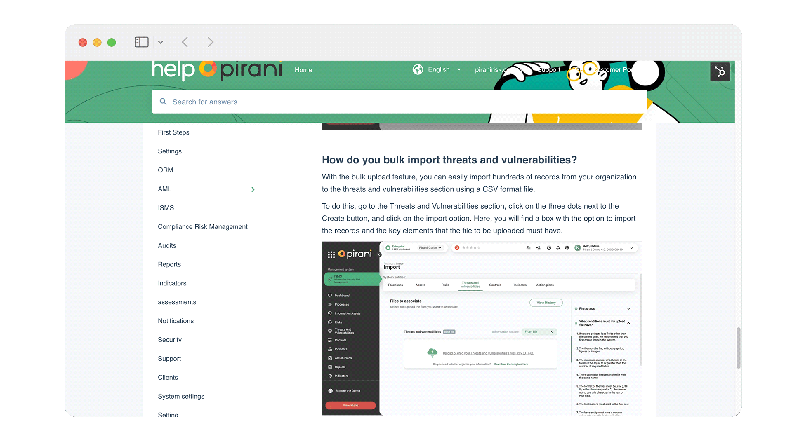
You can bulk import thousands of threat and vulnerability records into a single file, update them, and associate them directly with the corresponding information assets in a single upload.
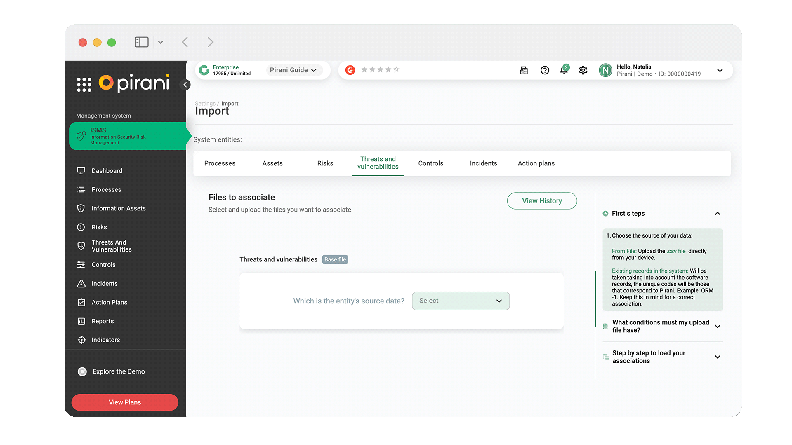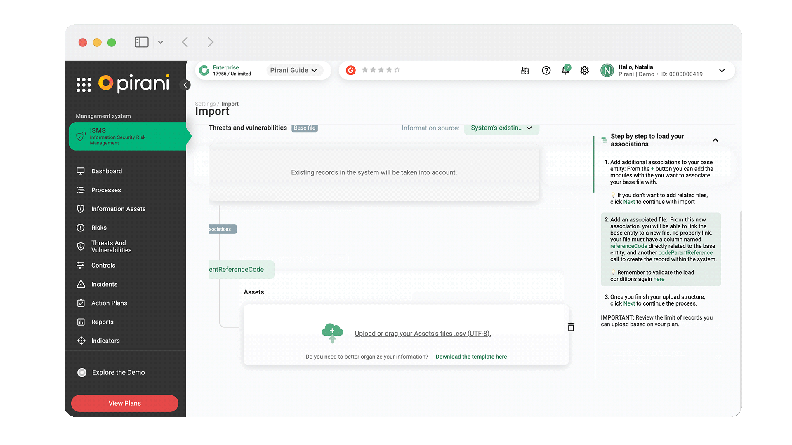
We created a detailed tutorial for you.
In this article, I described the main features of our threats and vulnerabilities section. However, if you want to learn how to create the threats and vulnerabilities of your information assets in more depth, I have included this tutorial, which explains everything related to this topic in detail.
⚡ Remember that you can have this section from the Starter plan.
You May Also Like
These Related Stories

Unraveling Information Security Management Complexities

Measure the success of your risk software with KPIs

What is Cyber Threat Intelligence?

Classification and management of information assets

5 Tips for Effective Information Security Management
.webp)


No Comments Yet
Let us know what you think