How to rate risks using the control matrix approach

In a previous article, we discussed how to identify risk by designing a control matrix. The identification of the risks is followed by their rating and assessment. To do so, there are also several approaches that aim to find a value to prioritize them according to criteria of frequency and impact through different techniques. One of them is the control matrix approach.
Control matrix
This approach is based on the identified threats and components, and consists of prioritizing both variables according to the evaluators' criteria and their importance for the company's objectives.
In order to carry out the rating, it is necessary, in the case of components, to know their level of importance for the processes or for the company and the project. In the case of threats, we must look at how significant they are in relation to the components and the consequences thereof for the company, such as: damage, detriment, loss or impairment of the operation.
In order to undertake this approach, a figure similar to the one shown in the illustration is initially constructed and continued with the following procedure:
Prioritization of components
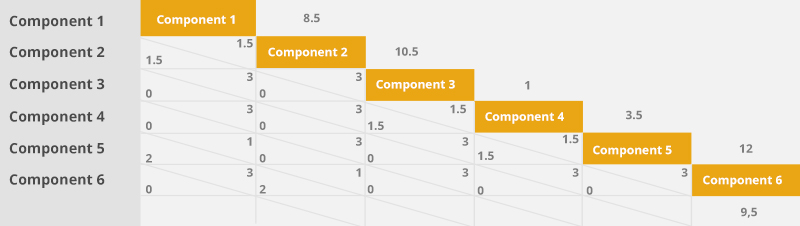
Mejía Quijano, Rubí. "Administración de riesgos, un enfoque empresarial", 2006, p. 77.
- First, the experts who identified the risks meet and compare all the components with each other and in pairs, i.e. component one is compared to component two and then to component three.
- At the meeting, each expert casts his/her vote for the component he/she considers most important. Each vote has the value of one.
- All the experts' votes are added up and the votes in favor of the column component are filled in the upper right-hand corner and those in favor of the row component are filled in the lower left-hand corner. For example, in the figure below, one expert voted for component one; another expert voted for component two; and the third expert divided his vote between the two.
- The process continues until all components are covered. At the end, the totals for each component are added and noted across from the cells on the diagonal line corresponding to each of them.
- When you have the totals by component, they are arranged from highest to lowest score. In case of ties, they are arranged in their respective order, one after the other.
Threats are rated in the same way as the components.
Prioritization of components and control threats
You May Also Like
These Related Stories

Excel Matrix vs. Risk Management Software: Which is better?

Main types of risk that can affect a company

Risk management for software projects
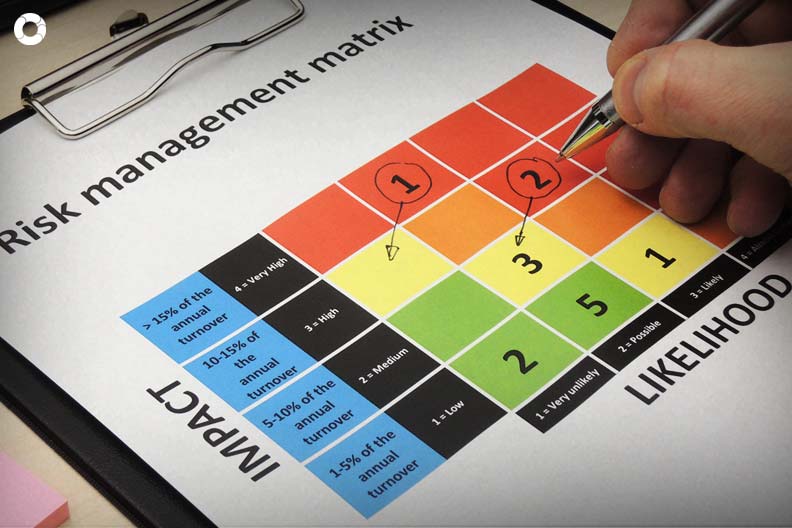
How to assess risk with a control matrix

Heat map: a tool to optimize risk management


No Comments Yet
Let us know what you think