Guide to conducting a risk analysis based on information assets
Introduction
When we talk about information security, we refer, according to ISO 27000 standard, to the set of procedures, activities, protocols, and policies that allow organizations to protect and preserve the confidentiality, integrity, and availability of critical, valuable, and sensitive information, both inside and outside the organization, thus reducing the possible impacts generated by the misuse or safeguarding of this information.
To achieve this, more and more organizations are putting into practice the guidelines of the ISO 27001 standard, a certifiable standard, for the identification, assessment, and management of information assets and the associated risks, thus seeking to safeguard information at all times.
In this sense, asset-based risk analysis and evaluation allows organizations that adopt this international standard to clearly identify all those threats that can negatively impact security objectives, as well as the image and reputation of the company.
For this asset-based risk analysis and evaluation, devices, hardware and software, databases, files, computers, and storage systems are considered, as well as people and other critical resources that must be protected to ensure the confidentiality, integrity, and availability of information.
In this Pirani Academy ebook, you will learn about key concepts of information security management, the steps to consider when conducting an asset-based risk analysis in your organization, and finally, we will share with you some of the advantages of having an adequate Information Security Management System (ISMS).
|
Table of Contents |
Key concepts in information security management
For effective management of information security in organizations, it's important to understand and have clarity about some key concepts:

1. Information asset:
Anything that has value for the organization and therefore needs to be protected. Assets can be tangible or intangible, such as IT infrastructure, auxiliary equipment, communication networks, facilities, and people, especially those with access to critical and sensitive information.
2. Confidentiality
Is one of the information properties that must be guaranteed. It has to do with the fact that information cannot be accessible or disclosed to those who are not authorized, meaning only those with a specific role and permissions can access it.
3. Integrity
The second property of information is maintaining the integrity of data as the sender originated it, there cannot be manipulations or alterations by third parties. In other words, the information must remain complete and accurate.
4. Availability
The third property of information refers to the fact that it must always be available to all personnel who have authorization to access it.
5. Vulnerability
A weakness or flaw in an information system that puts the security of the information at risk. Vulnerabilities largely depend on the nature of the systems and are an intrinsic factor to assets, which is why they can depend on hardware, software, networks, personnel, infrastructure, or the organization.
6. Threat
Anything that can affect/damage the security of an information system. The threats to an organization's information are varied, such as auxiliary infrastructure failures, computer-assisted fraud, employee unfamiliarity or misuse of information, equipment theft, espionage or vandalism, etc.
7. Incident
One or more unwanted and unexpected information security events that can significantly compromise business operations and threaten its security.
8. Information Security Management System (ISMS):
A management tool that allows an organization to establish, implement, monitor, review, maintain and improve information security for the achievement of business objectives.
In general, its main objective is to protect data, preserving its confidentiality, integrity and availability within the company and stakeholders. The ISMS consists of policies, procedures, guidelines, activities, and associated resources.
Steps for asset-based information risk analysis
After defining some of the key concepts related to information security, you can now learn about each of the recommended steps by ISO 27001 to perform a risk analysis in your organization based on information assets.
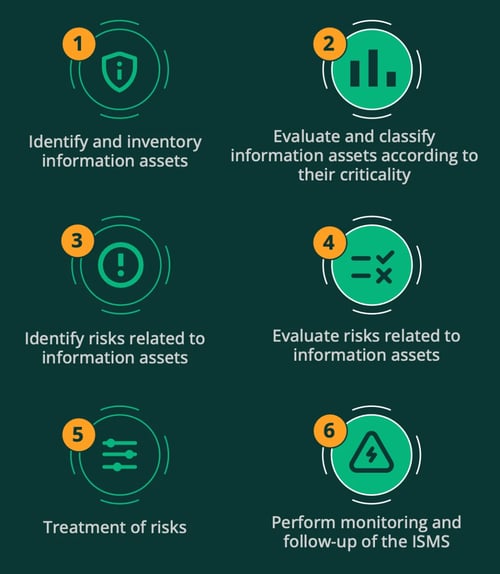
1. Identify and inventory information assets
The identification and inventory of information assets is the basis for the analysis and evaluation of information security risks.
This stage consists of identifying each asset that has some value for the organization and that is important to protect. This includes assets for processing, transmission, treatment or storage of information.
To do this, it is necessary to create an inventory that includes data such as:
- Asset name
- Description
- Asset type
- Associated process
- Owner
- Custodian
- Location
At this point, it is essential to define the asset's owner, i.e. the person or area responsible for it and therefore, the one who must establish and implement the measures and controls for its proper protection.
Having an up-to-date inventory allows organizations to have clarity on all their information assets and take the necessary measures to protect them.
2. Evaluate and classify information assets according to their criticality
Once the inventory of assets is complete, the next step is to evaluate and classify them according to their criticality. To do this, it is necessary to take into account the three properties of information: confidentiality, integrity, and availability, i.e. each of these should be classified with quantitative or qualitative variables, for example:
- Low: 10%
- Medium: 50%
- High: 100%
This helps determine the criticality of the asset and therefore, classify it.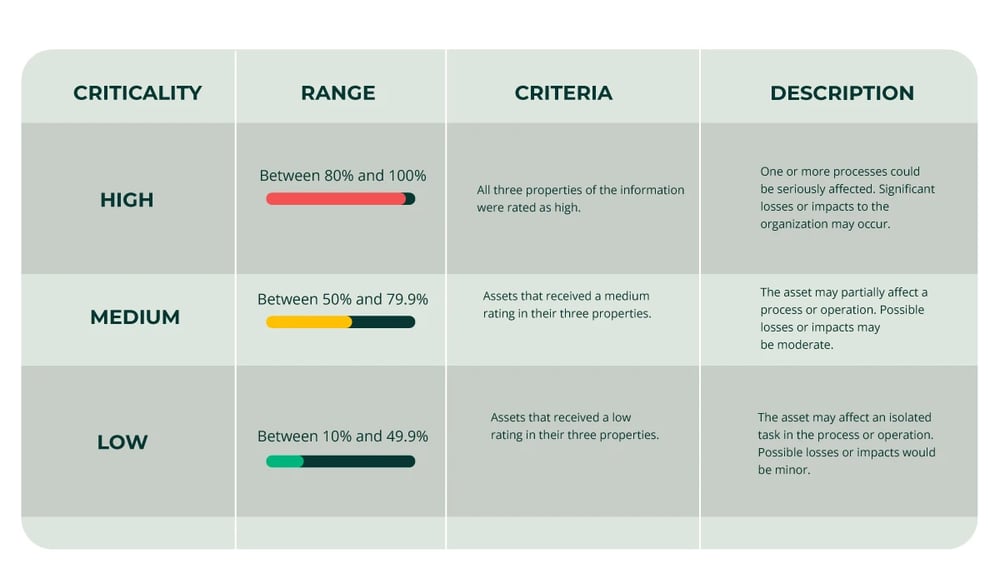
3. Identify information asset risks
The third step in information asset-based risk analysis is precisely identifying the risks to which the organization's assets are exposed, as well as the vulnerabilities and threats that can affect their confidentiality, integrity, and availability, as well as continuity of operation or service delivery.
Some information security risks may include: damage or alteration, loss, logical destruction, physical destruction, hacking, data kidnapping, or elimination
4. Evaluate information asset risks
After identifying the risks associated with each of the identified information assets, the next step is to establish both the probability of occurrence, i.e., the frequency with which they can materialize, and the impact they would have on the organization if they were to materialize.
Some impacts that may result from information security risks are financial losses, operational disruptions, damage to the image and reputation, among others.
When evaluating risks, the inherent risk is determined, and based on the level of each asset's rating, they are prioritized, for example, through a risk matrix, to establish the most appropriate controls and mitigation measures.
5. Treatment of risks
Once the inherent risk for each asset has been determined and they have been placed on the risk matrix, they must be given treatment. To perform this treatment, based on the impact analysis, it is necessary to define what action will be taken for each one of them:
- Accept the risk: take it on.
- Reduce the risk: minimize it by selecting and implementing controls.
- Transfer the risk: to have another entity take it on.
- Avoid the risk: stop using or eliminate the source asset where the risk would occur.
Generally, the most commonly used treatment action is to reduce the risk through the definition and implementation of controls that, on one hand, help to decrease the probability of occurrence and, on the other hand, the impact that it would cause if the risk materializes.
By implementing appropriate controls to protect information assets, the residual risk is obtained.
6. Perform monitoring and review of the information security system
In addition to the previous steps, taking into account what is stated in the ISO 27001 standard, it is essential to perform periodic monitoring and review of the entire information security management system because doing so allows for:
- Quickly identifying possible incidents.
- Detecting failures in procedures.
- Evaluating and measuring the effectiveness and efficiency of procedures and controls.
- Conducting internal audits on the ISMS.
- Analyzing internal and external scenarios that can affect the security of information assets.
- Making timely decisions to ensure the three properties of information are always guaranteed.
Advantages of the Information Security Management System
Information has become one of the main assets of organizations, which is why it is increasingly important to protect it and guarantee its three properties (confidentiality, integrity, and availability) at all times. An Information Security Management System (ISMS), such as the one proposed by ISO 27001, is of great utility for this objective.
- Among other advantages, implementing an ISMS in organizations allows:
- Reducing the risk of losses, theft, or corruption when handling information.
- Establishing a methodology that facilitates the management of information security.
- Defining security measures to allow customers, collaborators, and suppliers to access information in a secure and controlled manner.
- Generating optimal processes and procedures by offering guarantees on what needs to be done, how it needs to be done, and who needs to interact in each case.
- Promoting periodic external audits, which fosters continuous improvement of the system and the organization.
- Assuring clients, strategic partners, and suppliers that the organization is committed to ensuring the confidentiality, integrity, and availability of the information it manages and is entrusted with.
- Restoring the continuity of operations or service delivery as quickly as possible in the event of security incidents or cyber-attacks such as phishing, and ransomware, among others. In this way, the organization minimizes possible losses.
- Ensuring compliance with current regulations regarding personal information and intellectual
- property.Improving staff awareness of the importance of handling and properly protecting the information they have at their disposal.
- Providing a competitive advantage for the organization against its competitors because having an ISMS helps increase its national and international image.
Does your organization already have an adequate Information Security Management System? Discover how Pirani's ISMS can help your company have one and comply with ISO 27001.
Bibliographic references
- Norma ISO 27000
- Norma ISO 27001
- Escuela Europea de Excelencia: Cómo realizar una evaluación de riesgos basada en activos en ISO 27001
- Instituto Nacional de Ciberseguridad - INCIBE: Análisis de riesgos en 6 pasos
- Curso Pirani: Gestión de Seguridad de la Información
- Curso Pirani: Riesgos de Seguridad de la Información y Ciberseguridad

